Brewing the Kubernetes Storm Center: Open Source Threat Intelligence for the Cloud Native Ecosystem

- Why is Open Source Threat Intelligence Important?
- Introducing the Kubernetes Storm Centre
- How can Interested Parties Contribute?
This blog post summarises the KubeCon + CloudNativeCon Europe 2024 talk “Brewing the Kubernetes Storm Center: Open Source Threat Intelligence for the Cloud Native Ecosystem”, given by Dr Constanze Roedig, head of the Austrian Open Cloud Community, and Dr James Callaghan, Principal Consultant at ControlPlane. A full recording of the talk can be found here.
Why is Open Source Threat Intelligence Important?
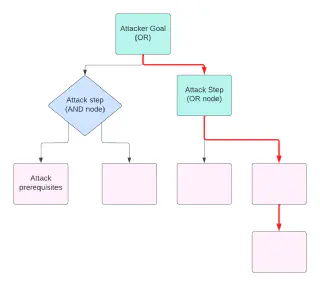
Accurate and up-to-date threat intelligence is crucial to threat modelling, as it helps us to understand how capable our adversaries are, and which types of attacks are currently being carried out in the wild. Currently, there are some good open sources of threat intelligence information, such as this database made available by Wiz. However, resources such as this often focus on individual events and particular CVEs that have been exploited. What if you want to quantify your own bespoke threat model, which may involve chaining together multiple types of attack?
Often when threat modelling, attack trees such as the example diagram above are created, which represent different paths an attacker could take in order to achieve their goal of compromising the system in question. To arrive at a quantified risk assessment, we must answer the question of how likely it is that an attacker traverses each path through the tree. Often this is achieved through making educated estimates, but wouldn’t it be nice if we had empirical evidence to back up our assessment? This is where the Kubernetes Storm Centre comes in!
Introducing the Kubernetes Storm Centre
The Kubernetes Storm Centre was conceived by Dr Constanze Roedig in the spirit of the SANS Internet Storm Centre, a program which monitors the level of malicious activity on the Internet, particularly with regard to large-scale infrastructure events. It is a newly formed open source initiative, with the aim of making cloud native threat intelligence available to everyone by encouraging organisations and individuals to run Kubernetes “honeyclusters”, and share their observations around suspected attacks.
This talk proposes an extensible method that, based on a given threat model:
- generates a Kubernetes-based environment with embedded trip-wires, enabling the detection of real attacker paths without interference,
- exposes these simulated environments to the wild to observe quantitative threat intelligence in action, and
- informs cost-effective decisions for a defensive team.
An example instrumented honeycluster showcasing a sample attack was demonstrated in the talk, and the repository can be found here.
How can Interested Parties Contribute?
Check out the Kubernetes Storm Centre Organisation on Github
Related blogs

FluxCon Atlanta Was Just the Start

Out on the GenAI Wild West: Part I - Red Team Redemption

