Walking the talks - ControlPlane at KubeCon Europe 2022
We were delighted to give five talks at this year’s KubeCon Europe in Valencia, as well as running the 4th consecutive CTF competition at the SecurityCon event on the first two days of the week.
Come to join us in North America for another CTF at SecurityCon and the opportunity to chat with our kind and intelligent colleagues at our booth!
A Treasure Map of Hacking (and Defending) Kubernetes
Andrew Martin (@sublimino)
In this ultimate guide to threat-driven defence, we threat model Kubernetes and detail how to attack and defend your precious clusters from nefarious adversaries. This broad and detailed appraisal of end-to-end cluster security teaches you how to defend against a range of historical and current CVEs, misconfigurations, and advanced attacks:
- See the historical relevance of CVEs and demonstrations of attacks against your containers, pods, supply chain, network, storage, policy, and wider organisation
- Understand when to use next-generation runtimes like gVisor, firecracker, and Kata Containers
- Delve into workload identity and advanced runtime hardening
- Consider the trust boundaries in soft- and hard-multitenant systems to appraise and limit the effects of compromise
- Learn to navigate the choppy waters of advanced Kubernetes security.
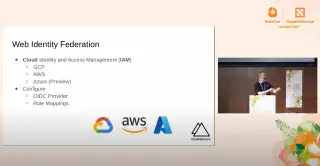
Throw Away Your Passwords: Trusting Workload Identity
Ric Featherstone (@ric_says)
Trust is required to secure our systems: we need it to bootstrap infrastructure, to run workloads, and to reassure our customers of their privacy. But how do we establish and secure this “trust” in a dynamic cloud native system?
Historically we relied upon identifiers such as IP addresses, passwords, and certificates, but can we do better than these antiquated authentication mechanisms? In this talk we:
- Demystify machine identity and its relationship to secrets management and access control
- Discuss the issues with historical approaches in a cloud native environment
- Solve the “bottom turtle” trust bootstrap quandary
- Appraise the open source implementations and technologies available to you
- Demonstrate practical examples of how to acquire a workload identity or secret zero
- Strive for a world in which passwords and static keys are replaced by dynamic credentials and hardware roots of trust
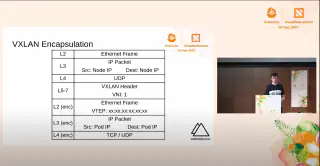
Three Surprising K8s Networking “Features” and How to Defend Against Them
James Cleverley-Prance (@jpts_)
Kubernetes’ networking model simplifies the user experience, but abstractions can introduce and hide complexity under the hood. This talk challenges perceived trust boundaries in Kubernetes networking and demonstrates some non-obvious and counter-intuitive behaviours. Left unchecked, these issues can mean Kubernetes clusters present a wider attack surface than may be immediately evident. The talk will cover: _ The external attack surface of a Kubernetes node _ Enumerating externally available cluster information _ Exploiting Linux networking to access internal pods and services _ Misusing CNI configurations to access internal pods and services You will gain an understanding of these attacks and how to use them, learn mitigation strategies and pragmatic defences, and be able to protect your clusters to avoid compromise.
Tweezering Kubernetes Resources: Operating on Operators
Kevin Ward (@wakewarduk)
Operators have become prevalent for the automation of repeatable cluster operations, replacing engineers in the Kubernetes configuration process. Although removing human error from the equation solves repeatability issues, Operators are often highly privileged with namespace or cluster-wide access to change resources. A compromised operator allows an attacker to deploy custom workloads very discreetly, and a rogue resource could go completely undetected. This talk asks and shows “what’s the worst that could happen?” to Operators by: - showing you how to threat model core Operator functionality - demonstrating how an Operator-based attacker can modify resources and gain persistence - how to securely appraise and test third-party Operators before trusting them - what to look out for during a code review or security related events.
Threat Modelling Kubernetes: A Lightspeed Introduction
Lewis Denham-Parry (@denhamparry)
Cloud native container and Kubernetes systems bring new threats and risks to our precious workloads. As cloud technologies undergo rapid innovation and new tools and techniques emerge, security can get left behind. The answer to this conveyor-belt of potential insecurity? Threat modelling! Join us for a primer on threat modelling cloud native systems, understanding adversarial techniques and preventative measures, and helping security and engineering teams increase the security and velocity of system delivery.
Related blogs

FluxCon Atlanta Was Just the Start

Out on the GenAI Wild West: Part I - Red Team Redemption