ControlPlane at OpenSSF and Open Source Summit Japan, 2023
By Jack Kelly
Firstly, our thoughts are with the people of Japan and the Ishikawa prefecture. As part of my trip, I visited the beautiful city of Kanazawa, Ishikawa in December and the news of the earthquake in the New Year was quite a shock. We hope the recovery efforts are going well and everyone affected is doing better.

Kenroku-en in Kanazawa, Ishikawa by Jack Kelly
Bookending 2023, ControlPlane went east; visiting the wonderful country of Japan for OpenSSF Day and Open Source Summit (OSS).

Ariake Central Tower by taka_jp - CC BY-SA 2.0
Both events were at the Ariake Central Tower located in Tokyo Bay, on the reclaimed land of Kōtō City within Tokyo. Ariake is a fantastic location for conferences, but a bit out of the way from central Tokyo; this is handy if you need to save the exploring for later and finish up some slides!
OpenSSF Day
OpenSSF Day was rich with important conversations around Software Supply Chain Security and OpenSSF projects, including talks on CVE trends for the last 17 years and associated threat actors, the Open Source Security Sandwich from Mike Lieberman at Kusari. Check out the schedule to see all the talks and slides from the day.
Integrating Existing Build-Tools with Sigstore: How It Went and What’s Left to Do - Jack Kelly

The slides can be found here
After a series of great talks, it was my turn to cover SLSA requirements and Sigstore tooling in the build pipeline.
The problem comprises separate layers that we may be familiar with from building software:
- Building the software
- Building the container
- CI platform doing the build
Attendees learnt that for SLSA 1 and 2 and using Sigstore tooling there’s not much that needs changing and your CI platform can do most of the heavy lifting.
The next part was detailing what that entails; what kind of work the CI platforms need to do for us to meet various SLSA levels and how we could do that ourselves if we could change our CI platforms.
We explored what data is of interest for provenance, and where we can get that data. Additionally, we looked at where we could integrate artefact signing at the platform level, outside of our build pipelines.

Wrapping up the talk there was a moment taken to think about what really is the difference between scripting a software build, a container build, and writing a pipeline.
This helped to explain nix’s approach to linking together builds, what a nix “derivation” is, and how this functional model can cover these 3 layers.
There were some hiccups being my first large talk, and tempting the demo gods so many times, but overall it was a great experience. In presenting this talk and watching the other great presentations, I learnt a lot and have plenty of ideas for improvement.
Open Source Summit
The next day was the beginning of the Open Source Summit, where there were plenty of familiar faces from the day before and many new faces.
The first day opened with keynotes, and an insightful chat between Linus Torvalds and Dirk Hohndel. The ever-popular topic of Rust in the Linux kernel came up and the conversation is generally a must watch for anyone who missed it.

For the second day’s round of keynotes there was a heartfelt presentation from Greg Kroah-Hartman on vulnerabilities in the Linux kernel, and the demand for CVE ratings causing frustration for kernel developers. Personally, I agree with Greg K-H, as fundamentally any bug of any sort in something as critical as the kernel can likely be utilised for attack and result in high-risk CVE. Tracking every single case is likely more effort than it’s worth and just enforcing the latest stable or LTS kernel is the best advice.
Following the keynote, I stuck around to snag a photo with Greg K-H and we had an interesting conversation continuing the topic of the keynote along with staff from CISA.

You can check out the whole schedule and check slides and links to recording on the sched.
Talks
The Road to Zero CVEs: People and Technology - Andrew Martin (ControlPlane) & Michael Lieberman (Kusari)

Andy and Kusari’s Michael Lieberman combined forces to discuss the technology, people, and plans to achieve the mythical “Zero CVEs”.
The talk is chock-full of Software Supply Chain Security info on tooling and processes and is well worth catching up on. You can watch this talk on YouTube.
Kubernetes AI Security Playbook: Safeguarding the Data and Model Supply Chain - Andrew Martin & Jack Kelly

On the second day it was time for Andy and I to cover the Threat Modeling work ControlPlane had done analysing risks to models on Kubeflow and their data.
We identify the type of AI we’re talking about and review the problem space.
And next is the fun part, we imagine we work for a company with many satellites in space. From these satellites we have a large amount of data and metrics being reported back to base-stations on the earth, and collated in our data centres.
From here we set a scope focusing on the Data Scientists, Data Engineers, and a the Kubeflow setup. And with a scope in place we review all manner of attack vectors throughout the process, followed by a range of potential mitigations.
There are a lot of parallels with securing a software pipeline, where we want to instil confidence in our inputs, our processes, and securing our outputs. However unlike software the size of this data are orders of magnitude bigger so some slightly different controls are necessary.
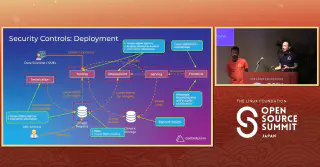
If this talk sounded interesting to you Kubeflow is up for security review in TAG Security in the coming months, and you’re welcome to collaborate or observe our open threat modelling process.
Here’s this talk on YouTube..
Wrapping Up
The booth crawl was very busy with a lot of Automotive Linux demos and other fun displays. I spotted a SteamDeck on one of the booths.

And of course the Penguin mascot from LinuC training was extremely popular.
In my trip around Japan following the conference I raised my confidence levels in speaking some of the Japanese I’ve learnt. Next time I’m planning to be more proactive in my networking and let people know I’m up for a chat in Japanese!
日本語まだまだ勉強中、その時はよろしくお願いします。
ControlPlane’s conference schedule is just getting started with State of Open Con in February, and we look forward to seeing you at the CTF in Paris @ KubeCon EU!
