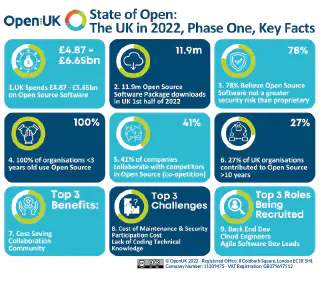
OpenUK Reports on the State of Open: The UK in 2022
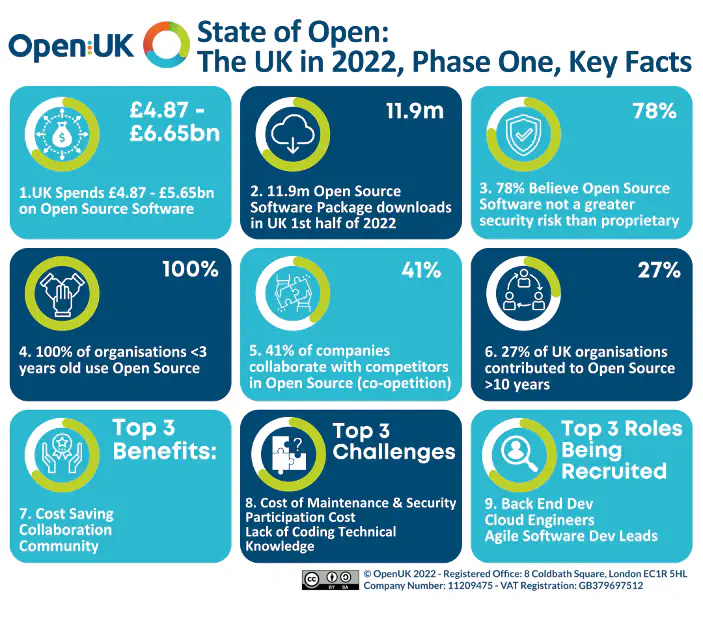

The OpenUK report is a yearly publication that provides an overview of the state of open source software and hardware in the UK. It covers economic impact, legal and policy issues, and community engagement.
Andrew Martin, ControlPlane CEO and pro-bono CISO for the charity, shared an updated on the state of open source security.
The report is available here with further information on the OpenUK website.
The State of Open Source Security, 2022
Andrew Martin, Founder and CEO ControlPlane and CISO OpenUK
Since our last report in October 2021, the online security landscape has changed significantly. November saw the internet catch fire with the infamous Log4shell vulnerability reminding us of the value of security assessing and patching critical projects, while December saw the OpenSSF’s “Great MultiFactor Authentication Distribution Project” hand out hardware security keys to open source developers. January then saw the commencement of hostilities between Russia and Ukraine, widening the threat landscape internationally and bringing nation state capabilities into sharp relief for producers and consumers of software everywhere.
In this more hostile landscape Open Source Software usage has remained a constant. Its use continues to rise in the private sector and governments despite the growing concerns about its provenance and veracity. January saw the OpenSSF brief the White House on software supply chain integrity, addressing the challenge of defending long and meandering developer and infrastructure supply chains, and advocating for Software Bills of Materials (SBOMs).
The snowballing adoption of SBOMs and the accompanying SPDX standard has not come as a surprise to the Open Source community, who have been managing software composition risk in distributions and the kernel for decades. Along with other emerging standards like Open Chain (simplifying open source trust and compliance), these projects represent years of steady effort and industry education.
Shipping an SBOM with a vendor or open source project is a signal that developers may understand the complex nature of software composition, and potentially a positive indicator of the safety of their software’s build and distribution processes. SBOMs are not a panacea, but one piece of the complex puzzle of modern software security that was brought so strongly into focus by the SolarWinds and Colonial Pipeline incidents at the start of 2021.
Alongside composition, the nature of human identity and beneficial ownership in Open Source has also come under scrutiny, as we attempt to decloak and unmask potentially hostile parties masquerading as benevolent contributors. Identifying developers under potential hostile regimes may put them at risk, so the challenges of preventing collusion are balanced with the need to maintain a free and open contributor network.
As for hostile contributions, a research team from the University of Minnesota attempted to ship malicious patches into the Linux Kernel, which tested the boundaries of ethical academia. They were detected and rejected (with the exception of an accidentally non-malicious patch, which was merged), but the kernel maintainers’ person-hours expended to identify and correct the contributions were non-trivial.
This highlights another great dichotomy in Open Source: the good faith and positive intent shown by maintainers, in the light of the cost of their time.
In an effort to balance this equation, the Alpha Omega project was launched in February to distribute funds and support to maintainers of critical Open Source Software, with an ambition to secure 10,000 open source projects with automation and scanning, and an initial core focus on Node.js’s vulnerability and dependency management, release process, and security patching and releasing.
Funding is imperative for these Open Source maintainers, who are often asymmetrically imbalanced against the large organisations that consume their projects, and unable to cope with security disclosure and management requirements those consumers may require. The OpenSSF is also looking to address this by offering a Security Incident Response Team (SIRT) of last resort, providing management for open source projects that have neither the funding, time, nor inclination to handle vulnerabilities disclosed to them. The void between widely-adopted but unfunded open source projects and their consumers is being closed by these efforts, as maintainers are being proactively assisted with patches, scanning, and management of vulnerability.
And funding is coming not just directly from consumers but also from the OpenSSF and its sponsors. The Open Source Summit, North America, brought together supply chain practitioners across the community at the OpenSSF Day to discuss SBOMs, securing critical software projects, and curated open source. The summit also included SupplyChainSecurityCon, focused on the implementation of supply chain fixes and emerging tools in the space.
Looking forward, September’s European-based Open Source Summit in Dublin also hosts another OpenSSF day, as well as a Supply Chain Security Con. It will be followed on September 20 by an OpenUK event in London, to bring the relevant practitioners together to address government and industry.
Following these solution-focused events, the OpenUK Summer of Open Source Software Security brings our own friends and colleagues across OpenUK, OpenSSF, and US Government to support UK Government on their response to the open source and supply chain security issues of the past year. With a series of presentations and open discussion, we look to build on our existing collaborations and assist the government and policymakers with the complex issues of open source legislation: if we can convince the UK to sponsor security fixes and maintainers of open source projects we will have achieved a significant milestone for the industry in the UK.
Finally, we look forward to February 2023, when the OpenUK conference in London hosts Security and Government work streams. We have a busy year ahead, and with the existing kind collaboration fostered between businesses and governments across Europe and the Atlantic the future for the challenges of Open Source Security has never looked brighter.
Contributing Authors
- Sarah Murphy, MS, Welsh Parliament
- Amanda Brock, CEO, OpenUK
- Bruce Perens, one of the founders, Open Source Software Movement
- James Parker, Community Planning & Engagement Service, and Michael von Euw, Head of Applications, Scottish Tech Army
- Gyda Carmichael, Head of Data Programmes, The Scottish Government
- Thomas Williamson, Technical lead, The Scottish Government
- James Stewart, Partner, Public Digital
- Phil Tudor, Head of Applied Research for Infrastructure, Rob Cooper, Producer, BBC R&D
- Simon Phipps, Director of Standards Open Source Initiative
- Judy Parnall, Head of Standards and Industry, BBC R&D
- Christian Martorella, Chief Information Security Officer
- Seiji Okamoto, Cloud Platform Engineer at Nationwide Building Society
- Ed Alford, Chief Technology Officer, New Look
- Simon Goldsmith Director of Information Security, OVO
- Andrew Martin, Founder and CEO ControlPlane and CISO OpenUK
- Eric Brewer, Google Fellow, Google
- Cristian Parrino, Chief Sustainability Officer, OpenUK
- Dr Jennifer Barth, Smoothmedia

