Secure Kubernetes and Container Platforms
Cloud Native Penetration Testing Services
Gain expert insight into your security posture with our penetration testers.
Offensive Security and Penetration Testing
Kubernetes and Containers
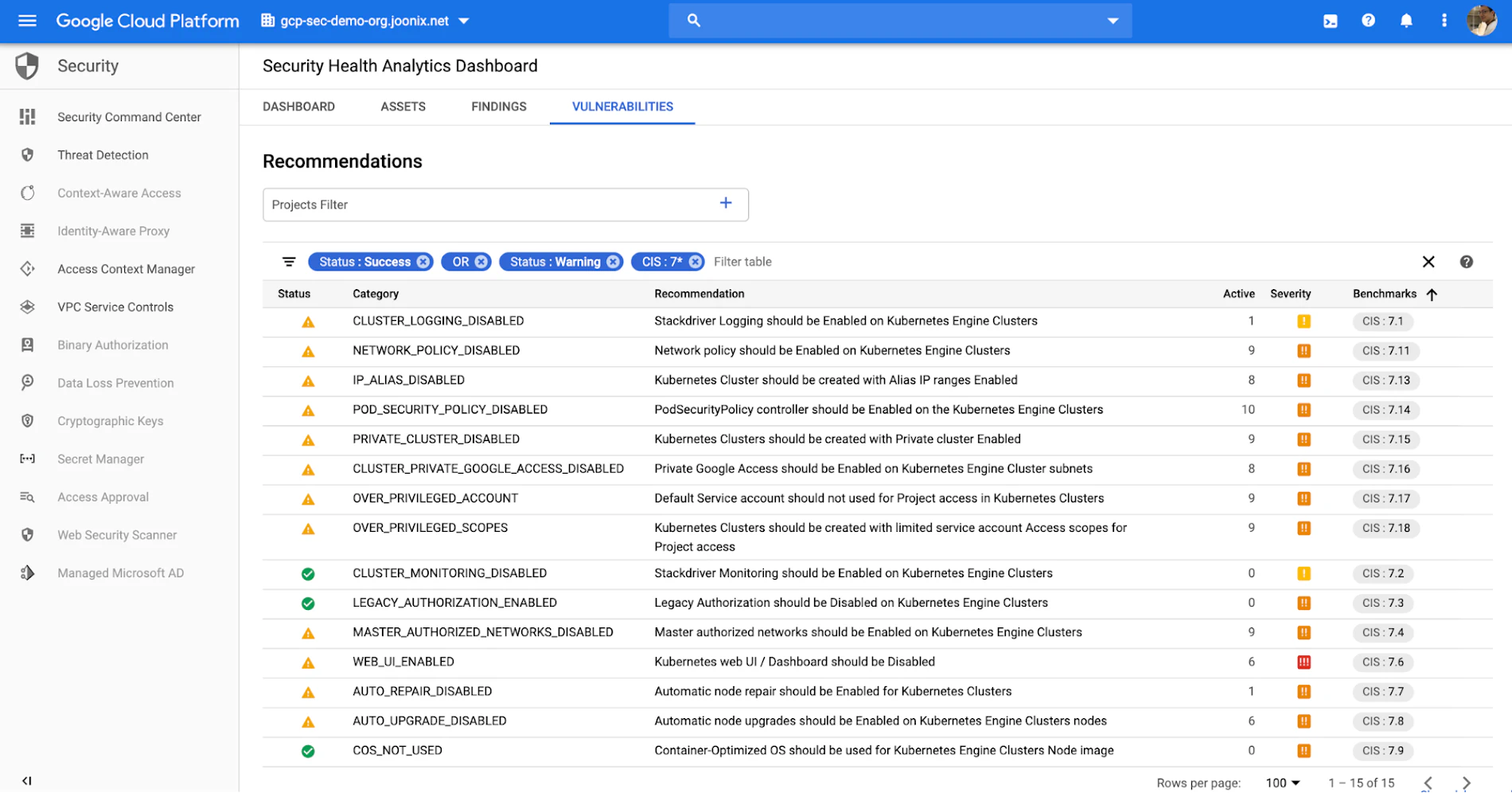
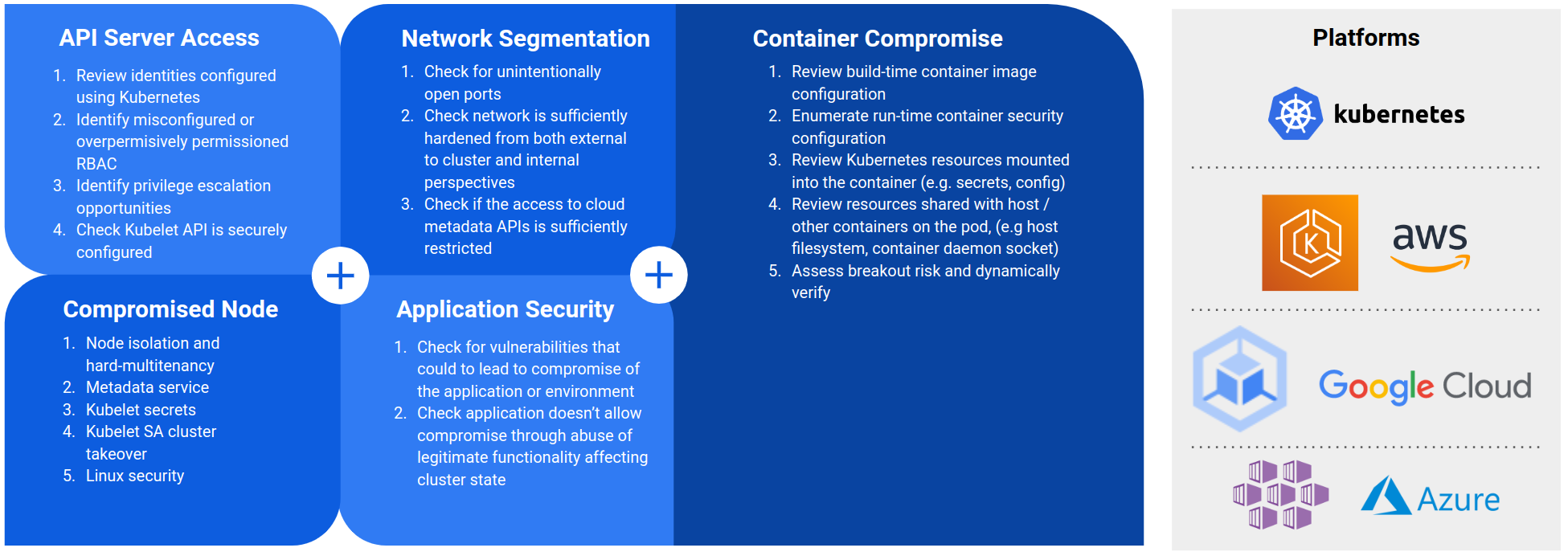
Assess Kubernetes at multiple levels, from underlying nodes to API access and cloud integrations. AWS EKS, GCP GKE, Azure AKS, OpenShift, and on-premise deployments.
CI/CD and Progressive Delivery
Evaluate the security posture of systems involved in the release process, from source code to production. GitHub, GitLab, Jenkins, Tekton, and more.
Hacking Kubernetes Training and CTFs
Learn Kubernetes security fundamentals, risks to clusters, and how to validate security configurations. Access cloud-hosted clusters for hands-on experience.
Selected Work
 Kubernetes Certified Solutions Provider
Kubernetes Certified Solutions Provider Kubernetes Training Provider
Kubernetes Training Provider
Why Choose Us
ControlPlane's Expertise
It can be challenging to understand where critical risks reside.
We provide insight into the security posture of cloud native environments, evaluating configuration for vulnerabilities, assessing systems against key threats, and delivering practical remediation actions.
- 7+ Years of Experience
ControlPlane has worked with regulated industries globally, providing in-depth expertise in cloud native technology and supply chain security solutions for more than seven years.
- Industry Leadership
Our CEO co-authored 'Hacking Kubernetes', a practical guide to Kubernetes security, and we run the KubeCon Capture the Flag experiences for the Linux Foundation. We've provided training from fundamentals to advanced security for highly regulated clients.
- Community Leadership
ControlPlane authored the CIS GKE Benchmarks and is active in the open source community, providing security assurance, patches, and testing for cloud native projects.
Need something different?
Our team tackles unique, challenging security assessments. From isolated execution environments to internet-scale infrastructure, we provide insight into complex and cutting-edge systems.