Secure Kubernetes and Cloud, Faster
Assess and enhance the security of your delivery and systems.
Kubernetes and platform hardening in cloud or on-prem.
Cluster Security Health Check
Security essentials to get you in production, fast
1 week fixed cost
A single cluster assessment
- Executive summary
- Detailed categorised findings
- Actionable recommendations
Cluster Fleet Threat Model
Popular
A roadmap securing your entire Kubernetes fleet
3 weeks fully customisable
For organisations scaling operations around a single cluster technology
- Everything in Cluster Security Health Check
- Comprehensive attack trees
- Fleet risk review
- Controls mapping
- In-depth remediations
- Collaborative roadmap
Container Security Maturity Assessment
End-to-end security for Kubernetes and containers
Call us bespoke package
To asses multiple orchestration platforms
- Everything in Cluster Fleet Threat Model
- Detailed maturity assessment
- Security level report
- Strategic work streams for remediation
- SOC integration and collaboration
- Ongoing support and assistance

Threat Models
Move to production faster and more securely, customised to your risk tolerance and existing mitigations.
Know your adversary
Threat modelling finds and addresses problems early in the SDLC.
- Reduce Risk
- Minimize risk by identifying and mitigating security vulnerabilities
- Minimise Costs
- Avoid costly rework, system downtime, legal liabilities, and reputational damage
- Compliance and Regulatory Conformance
- Identify potential gaps in security and data protection
- Improve Stakeholder Confidence
- Stronger relationships, increased customer trust, and enhanced brand reputation
Attack Trees Illuminate Vulnerabilities
Gain insight into potential attack paths with an easily understandable format. Engage stakeholders in the threat mitigation process to prove security ROI and ensure alignment on priorities.
Share a visual language
Navigate complex attack scenarios with ease
Understand your controls
Map attack vectors and implement countermeasures
Quantify governance, risk, and compliance
Manage risks in order of precedence
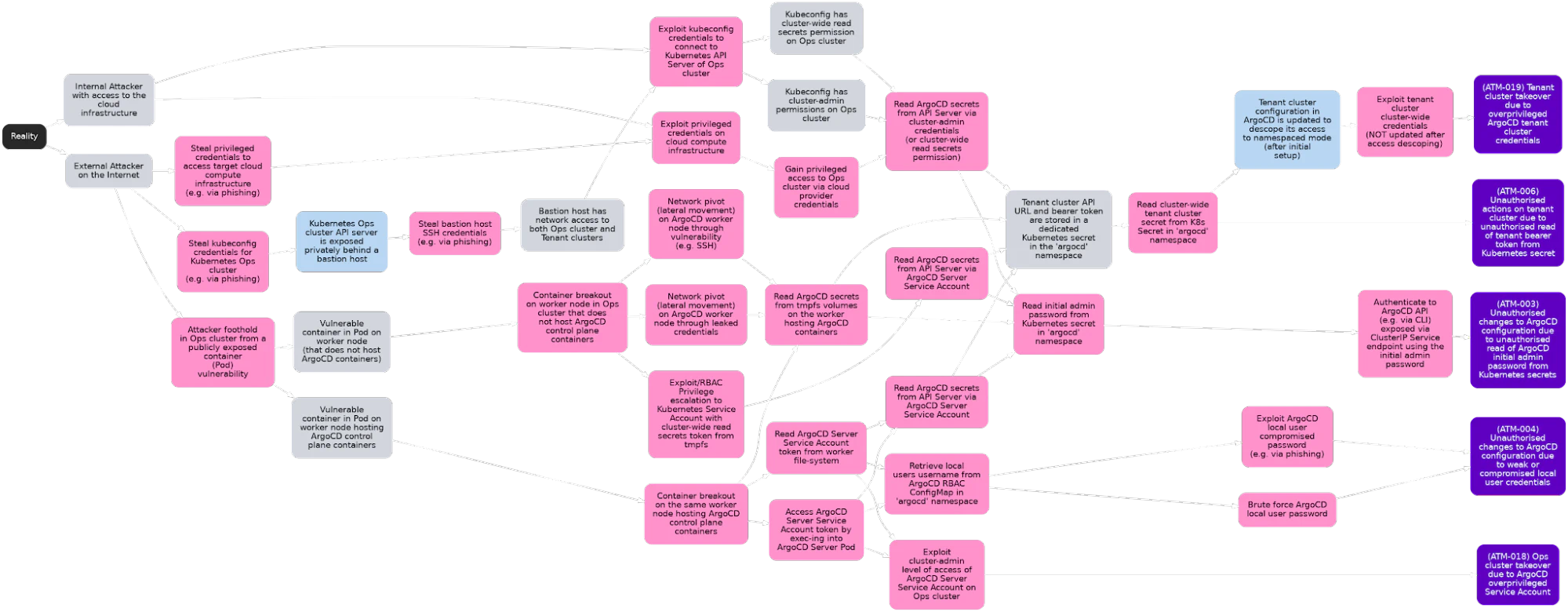
Threat Model Package Comparison
Our packages build on each other to provide the level of support you need.
| Offering | Environment | Key Focus | Outputs |
|---|---|---|---|
| Cluster Security Health Check | Single cluster, prior to go-live | Quick identification and remediation of key deficiencies | Slide deck presentation |
| Cluster Fleet Threat Model | Multiple clusters using a single container orchestration platform | Comprehensive analysis of the security threats facing the organisation’s clusters supported by a remediations roadmap | Detailed threat modelling and remediation report |
| Container Security Maturity Assessment | Container-based workloads in an organisation | Organisational control assessment against industry-standard frameworks and identification of strategic remediation workstreams | Maturity assessment report, threat model report, strategic workstream proposals |
Fast-Track Your Single Cluster Security
Accelerate your single cluster security with laser-focused assessments providing immediate results.
Advantages
- Expert-guided, tailored assessment
- Immediate communication of flaws
- Quick wins for tight deployment deadlines
Who’s it For?
Organisations nearing deployment or in need of a security sprint.
- Single cluster operations
- Preparing to go live
- Regulatory needs
Customer Journey
From vulnerability scenarios to hands-on remediation, we guide you through every possibility and recommended option.
- Scenario-based threat modelling
- Remediation support
- Penetration tests
Navigate Complexity, Optimize Security
Dive deeper into the labyrinth of your multi-cluster environments. We decode complexity, offering custom solutions for your unique challenges.
Advantages
- Customised wide-scale cluster analysis
- Comprehensive security and operational insights
- Actionable roadmap to remediate concerns
Who’s it For?
Organisations navigating the intricate web of multi-cluster operations using a single container orchestration platform.
- Multiple cluster setups
- Tech discovery phases
- Regulatory compliance support
Customer Journey
We’re not just advisors; we’re your security partners. From actionable threat models to long-term maturity plans, we have you covered.
- Detailed low-level attack trees
- Offensive security capabilities
- Prioritised risk ledger
- In-depth remediations and controls
- Collaborative roadmap
Secure Your Containerized Applications
Defend your entire Kubernetes and container estate. We align your security strategies with industry benchmarks for threat-resilient deployments.
Advantages
- Dedicated access to industry-leading SMEs
- Comprehensive benchmarking and assessment
- Ongoing strategic work stream collaboration
Who’s it For?
Organisations with governance and compliance requirements looking to unify their container strategies across a multi-platform estate.
- Large containerized application deployments
- Regulatory and compliance goals
- Security and development harmonisation
Customer Journey
We turn recommendations into actions and actions into habit, ensuring your container security continues to mature throughout system lifecycles.
- Best-in-class Kubernetes and container security assessment
- Extensive threat models, attack trees, and GRC documentation
- Controls, guardrails, and recommendations mapped to capabilities
- Offensive security and penetration testing options
- Integration with SOC and SIEM automation
- Comprehensive engineering support for implementation
- Regular updates and full training for your organisation
- Full security aftercare, ensuring your long-term resilience
Don't Just Take Our Word For It: Read Our Success Stories
We've secured thousands of clusters for some of the world's most secure companies and clouds.
Reduce intrinsic risk and capital expenditure
Industry Leading Threat Modelling Expertise
- Direct access to a team of experienced professionals
- Evaluation of container security controls against industry standards
- Tailored assessment to meet your unique needs and requirements
- Actionable recommendations for remediation and a roadmap for improvement
Frequently asked questions
Don't see your question? Email us: [email protected]
Threat modeling identifies high-risk system areas before or during development, reducing costly late-stage fixes revealed by penetration testing. It offers deeper insights than existing documentation and tailors security measures to data sensitivity.
Threat models focus on select concerns and actors, allowing for time-bound completion. We tailor the scope to meet your schedule, delivering targeted insights when you need them.
Yes, all packages are customisable to your needs, and complemented by our penetration testing and architecture services.
